The saga layout pattern is a way to manage data uniformity throughout microservices in distributed purchase situations. A saga is a sequence of transactions that updates each service and also publishes a message or event to trigger the next deal step. If an action fails, the saga carries out making up transactions that counteract the preceding transactions.

Context and problem
A transaction is a single unit of logic or work, sometimes made up of multiple operations. Within a transaction, an event is a state change that occurs to an entity, and a command encapsulates all information needed to perform an action or trigger a later event.
Transactions need to be atomic, consistent, isolated, as well as durable (ACID). Transactions within a single service are ACID, however, cross-service data uniformity requires a cross-service transaction management method.
In multiservices architectures:
- Atomicity is an indivisible and irreducible collection of procedures that should all happen or none happen. .
- Consistency suggests the transaction brings the data only from one valid state to one more legitimate state. .
- Isolation assurances that concurrent transaction create the exact same data state that sequentially performed transactions would certainly have produced
- Durability ensures that committed transactions remain committed even in case of system failure or power outage.
A database-per-microservice model offers several benefits for microservices architectures. Encapsulating domain data lets each solution utilize its finest data store kind and also schema, range its very own data shop as necessary, and be shielded from various other service failures. Nonetheless, making certain data uniformity throughout service-specific databases poses challenges.
Dispersed transactions like the two-phase commit (2PC) protocol require all individuals in a transaction to devote or curtail prior to the transaction can continue. Nevertheless, some individual applications, such as NoSQL databases and also message brokering, do not sustain this design.
Another distributed transaction limitation is interprocess communication (IPC) synchronicity and also schedule. Operating system-provided IPC enables separate procedures to share data. For dispersed transactions to dedicate, all taking part services should be available, possibly reducing general system availability. Building applications with IPC or transaction restrictions are candidates for the saga pattern.
Solution
The saga pattern offerstransaction administration using a sequence of local transactions. A local purchase is the atomic work initiative done by a saga individual. Each local transaction updates the database as well as publishes a message or event to trigger the next local transaction in the saga. If a local transaction stops working, the saga carries out a collection of making up transactions that undo the modifications that were made by the coming before local transactions.
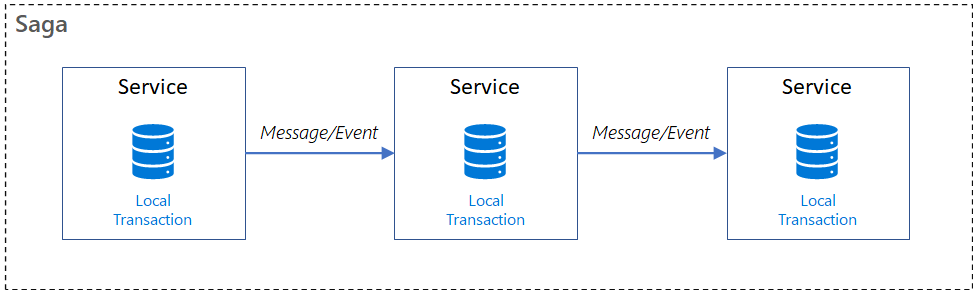
In saga patterns:
- Compensable transactions are transactions that can possibly be reversed by processing one more transaction with the contrary effect.
- A pivot transaction is the go/no-go point in a saga. If the pivot transaction commits, the saga runs until completion. A pivot transaction can be a transaction that is neither compensable nor retryable, or it can be the last compensable transaction or the first retryable transaction in the saga.
- Retryable transactions are transactions that follow the pivot transaction and are guaranteed to succeed.
There are two typical saga implementation strategies, choreography and orchestration. Each method has its own collection of challenges and technologies to work with the operations.
Choreography
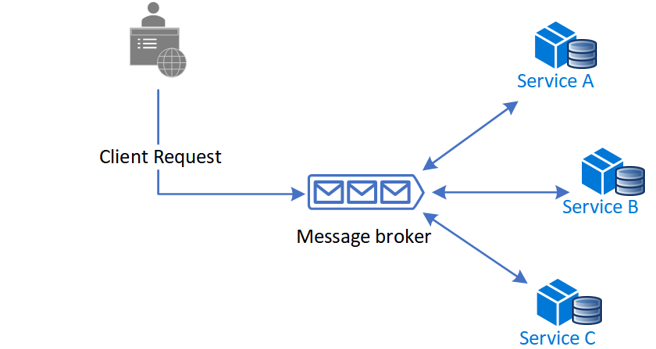
Choreography is a way to coordinate sagas where participants exchange events without a centralized point of control. With choreography, each local transaction releases domain name events that set off regional purchases in various other services..
Advantages
- Great for complex operations entailing many individuals or new participants added in time.
- Ideal when there is control over every individual while doing so, and control over the circulation of activities.
- Doesn’t introduce cyclical reliances, due to the fact that the orchestrator unilaterally depends upon the saga participants.
- Saga participants do not need to know about commands for various other participants. Clear splitting up of problems streamlines organization logic.
Disadvantages
- Additional style intricacy needs an application of a control logic.
- There’s an extra point of failing, due to the fact that the orchestrator takes care of the total operations.
Issues and considerations
Consider the following points when implementing the saga pattern:
- The saga pattern may originally be tough, as it requires a brand-new means of assuming on how to work with a transaction and preserve data consistency for an organization process covering multiple microservices.
- The saga pattern is specifically tough to debug, as well as the complexity grows as participants enhance.
- Data can’t be rolled back, because saga participants commit changes to their local databases.
- The execution needs to be capable of dealing with a set of prospective short-term failings, and provide idempotence for reducing side-effects and ensuring data consistency. Idempotence indicates that the exact same operation can be duplicated numerous times without changing the initial result.
- It’s ideal to implement observability to keep track of the saga operations.
- The absence of participant data isolation imposes resilience obstacles. The saga implementation must include countermeasures to reduce anomalies.
The following anomalies can happen without correct actions:
- Lost updates, when one saga writes without reading changes made by another saga.
- Dirty reads, when a transaction or a saga checks out updates made by a saga that has actually not yet completed those updates.
- Fuzzy/nonrepeatable reads, when different saga steps read various data since a data update occurs between the reviews
Suggested countermeasures to reduce or protect against anomalies consist of:
- Semantic lock, an application-level lock where a saga’s compensable transaction utilizes a semaphore to show an update remains in progression.
- Commutative updates that can be implemented in any type of order and also generate the exact same result.
- Pessimistic view: It’s feasible for one saga to review filthy data, while one more saga is running a compensable
- transaction to curtail the operation. Cynical view reorders the saga so the underlying data updates in a retryable transaction, which removes the opportunity of an unclean read.
- Reread value confirms that data is unchanged, and after that updates the document. If the document has actually transformed, the steps terminate and the saga may reactivate.
- A version file records the operations on a record as they arrive, and then executes them in the correct order.
- By value uses each request’s business risk to dynamically select the concurrency mechanism. Low-risk requests favor sagas, while high-risk requests favor distributed transactions.
When to use this pattern
Use the saga pattern when you need to:
- Ensure data consistency in a distributed system without tight coupling.
- Roll back or compensate if one of the operations in the sequence fails.
The saga pattern is less suitable for:
- Tightly coupled transactions.
- Compensating transactions that occur in earlier participants.
- Cyclic dependencies.
Example
Orchestration-based Saga is a saga implementation reference using the orchestration approach that simulates a money transfer scenario with successful and failed workflows.
Related patterns
The following patterns might also be useful when implementing this pattern:
- Choreography has each component of the system participate in the decision-making process about the workflow of a business transaction, instead of relying on a central point of control.
- Compensating transactions undo work performed by a series of steps, and eventually define a consistent operation if one or more steps fail. Cloud-hosted applications that implement complex business processes and workflows often follow this eventual consistency model.
- Retry lets an application handle transient failures when it tries to connect to a service or network resource, by transparently retrying the failed operation. Retry can improve the stability of the application.
- Circuit breaker handles faults that take a variable amount of time to recover from, when connecting to a remote service or resource. Circuit breaker can improve the stability and resiliency of an application.
- Health endpoint monitoring implements functional checks in an application that external tools can access through exposed endpoints at regular intervals. Health endpoint monitoring can help verify that applications and services are performing correctly.